Microsoft Direct Send phishing attacks explained
Barracuda security analysts recently detected a phishing campaign that leverages the Microsoft 365 Direct Send feature to bypass email security features. This is a large-scale attack that abuses a legitimate Microsoft 365 feature to impersonate internal communications. See the Barracuda Security Advisory and the Cybersecurity Threat Advisory for technical details on this attack.
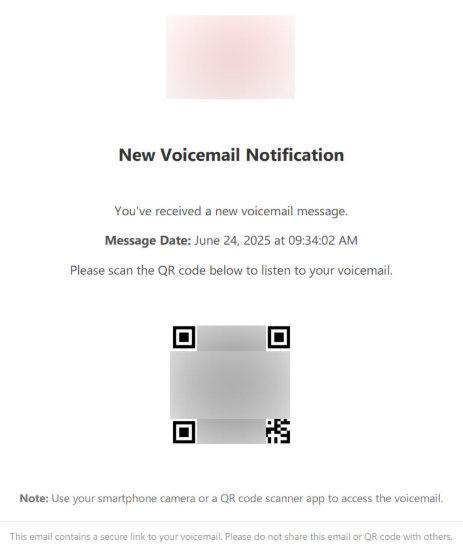
This phishing campaign presents a huge risk to unprotected companies using Microsoft 365. The messages impersonate an internal company email and carry a PDF attachment that includes a QR code. Recipients are instructed to scan the QR code so that they can access a voice message.
The QR code directs the victim to a fake Microsoft login form, which is where the threat actors will capture the user’s credentials. The stolen credentials will then be sold and/or used to kick off a larger attack against the company.
What is Direct Send?
Direct Send is an open email pathway that allows email to be sent without authentication. This is a legitimate but low-security Microsoft feature that allows non-email servers to send email. Most companies would use this feature to allow networked printers and business applications to email an individual in the same domain. You can find out more about it in this Microsoft Learn document.
The most important thing to note here is that Direct Send messages use internal infrastructure and do not need to pass email authorization and security measures. Direct Send traffic will not route through external email security gateways. You must take specific actions to secure Direct Send in your environment.
Microsoft introduced the "Reject Direct Send" feature in April 2025. This feature blocks all Direct Send traffic and is turned off by default. Using this feature may break legitimate business functions, so Microsoft urges administrators to use caution when enabling the feature.
What is the exploit?
It’s important to understand that this is not an unpatched vulnerability in any Microsoft or any third-party system. Our Cybersecurity Threat Advisory covers this in more detail:
This attack is particularly concerning due to several factors:
- Abuse of a Legitimate Feature: The attack leverages a built-in Microsoft 365 function, making it difficult to disable without disrupting business operations.
- No CVE Assigned: Since this is not a software vulnerability but a misuse of intended functionality, it lacks a CVE identifier, complicating tracking and remediation.
- Bypasses Email Security: Traditional email defenses relying on SPF, DKIM, and DMARC are ineffective against this tactic.
- Internal Sender Spoofing: Emails appear to come from trusted internal sources, increasing the likelihood of user interaction.
- Widespread Exposure: Any organization using Direct Send is potentially at risk.
Protect yourself
It is possible to secure Direct Send without rejecting all Direct Send mail. Barracuda Email Gateway Defense customers may have secured Direct Send when configuring the connectors for Microsoft 365. The steps to configure Direct Send security are in this Barracuda Campus article. This is a step-by-step walkthrough that takes only a few minutes to complete. You can also contact Barracuda Support for assistance.
If you are not absolutely certain that Direct Send has been secured, please follow the steps in the Barracuda Campus document or contact Barracuda Support.
Further resources:

The Ransomware Insights Report 2025
Key findings about the experience and impact of ransomware on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

Managed Vulnerability Security: Faster remediation, fewer risks, easier compliance
See how easy it can be to find the vulnerabilities cybercriminals want to exploit