Threat Spotlight: Split and nested QR codes fuel new generation of ‘quishing’ attacks
Quishing is a form of phishing that involves the use of QR codes embedded with malicious links. When scanned, these QR codes redirect victims to fake websites designed to steal their credentials or other sensitive information.
Malicious QR codes are popular with attackers for several reasons. They cannot be read by humans so don’t raise any red flags, and they can often bypass traditional security measures such as email filters and link scanners. Further, since recipients often have to switch to a mobile device to scan the code, it can take users out of the company security perimeter and away from protection.
As security tools adapt to the threat of quishing, attackers have continued to innovate their approaches. Barracuda has reported previously on the evolution of QR code phishing attacks and the arrival of more sophisticated ASCII QR code attacks.
In this article, we explore the latest advances in QR code attack techniques, including split QR codes and nested (QR-in-QR) codes.
Split QR codes
The Gabagool phishing-as-a-service (PhaaS) kit recently started using a new technique to help malicious QR codes evade detection. The technique involves splitting the QR code into two separate images and embedding them in a phishing email. When traditional email security solutions scan the message, they see two distinct and benign-looking images rather than one complete QR code.
Barracuda threat analysts recently found Gabagool attackers implementing split QR codes in an attack that began as a standard fake Microsoft ‘password reset’ scam. The attackers’ use of highly tailored messages suggests they’d previously implemented a successful conversation hijacking attack against the target.
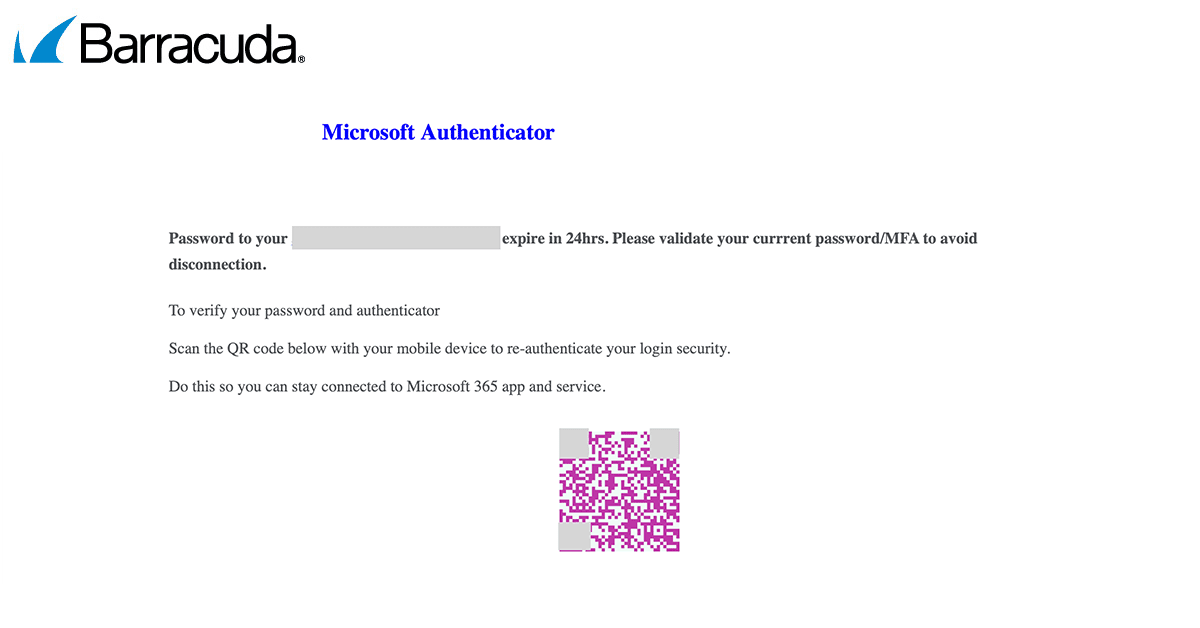

If the recipient scans the code, they are directed to a phishing page designed to steal their Microsoft login credentials.
Nested QR codes
Analysts have seen the Tycoon 2FA PhaaS deploy another novel technique to help malicious QR codes evade detection. In this instance the malicious QR code is embedded within or around a legitimate QR code.

The email above shows how the two QR codes are nested together. The outer QR code points to a malicious URL, while the inner QR code leads to Google. This technique can make it harder for scanners to detect the threat because the results are ambiguous.
Defending against evolving QR codes
Alongside the essential basics of security awareness training, multifactor authentication and robust spam and malware filters, organizations should consider multilayered email protection that integrates multimodel AI capabilities to detect such rapidly evolving threats.
Multimodal AI enhances detection by rendering attachment images to locate QR codes visually, decoding QR content and analyzing the destination URL or payload, executing suspicious links in sandbox environments to detect real-time malicious behavior, and using machine learning to analyze QR code structure and pixel patterns without needing to extract the embedded content.
Barracuda’s multimodal AI combines OCR, deep image processing and natural language models to detect image-based phishing emails — even those that contain only a QR code.
Barracuda’s threat analysts report regularly on evolving email threats and attack tactics. Subscribe to our blog for updates.

The Email Security Breach Report 2025
Key findings about the experience and impact of email security breaches on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

The MSP Customer Insight Report 2025
A global look at what organizations need and want from their cybersecurity managed service providers





