Why you should be familiar with the MITRE ATT&CK framework
Many technologists and IT pros are aware of MITRE ATT&CK, but they don’t know what to do with it. If you’re using tools like CIS CDM and NIST CSF 2.0, why would you need to know the details found in MITRE ATT&CK? While it’s true that you can get by without digging into it, understanding how to use MITRE ATT&CK can help you develop stronger and more agile defenses for your company.
What are MITRE and MITRE ATT&CK?
Let’s start with the organization. The full name is The MITRE Corporation, though most of us know it as MITRE. It was launched in 1958 when it transitioned from the MIT Lincoln Laboratory to an independent entity. Contrary to popular belief, MITRE does not stand for Massachusetts Institute of Technology Research and Engineering or (apparently) anything else.
According to Murphy, the incorporators claimed that the name was the French spelling of the English word “miter,” a smooth joining of two pieces. Many people have speculated that it stood for “MIT Research and Engineering,” but that would have flown in the face of Stratton’s clear desire to disassociate MIT from the work on SAGE. ~Simson Garfinkel, MIT's first divorce, MIT Technology Review
There is still some specultaion around MITRE as an acronym. One early employee recalls seeing cabinets labeled "MIT/RE" which may suggest MIT Research Establishment. MITRE leadership has always denied the name is an acronym. Check out the MIT Technology Review article for a history of the mystery around the name and all-caps styling.
Today MITRE is a nonprofit organization that operates federally funded research and development centers (FFRDCs) across multiple focus areas. The one we’re talking about here is cybersecurity.
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a globally accessible knowledge base of adversary behavior. In the simplest terms, it’s an encyclopedia of how threat actors operate in the real world.
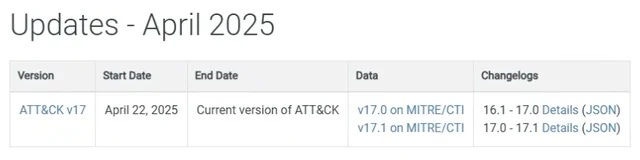
MITRE ATT&CK is regularly updated, with major updates released every six months, usually in the spring and fall. Minor updates occur as needed, but these are usually minor data adjustments or error/typo corrections. The ATT&CK content itself isn’t changed. MITRE ATT&CK versions and updates use a ‘major.minor’ version number. With every 6-month update, the major version number increments by 1.0. With every minor update, the version number increments by .1. For example, the most recent version of ATT&CK is 17.1. This is because minor updates were applied after version 17 was released.
Each major release of ATT&CK gets its own permanent webpage. The most current version always resides at https://attack.mitre.org/.
Tactics, Techniques and Procedures (TTPs)
Now we get to the good stuff. Most profiles of cyberattacks will include references to TTPs. If you aren’t sure what they are, here’s the simple explanation:
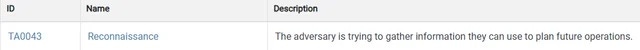
Tactics: The "why" behind an attack, or the reason that a threat actor does something. One example is the tactic of reconnaissance. The short description of this tactic is “The adversary is trying to gather information they can use to plan future operations.” Here is how it looks in the list of tactics:
The ID on the left – TA0043 – tells us that this is a Tactic Assignment (TA) and is the 43rd entry in the list of TAs. The ID numbers are assigned in sequence based on when the tactic was added. TA0043 was assigned after TA0042, for example. Each tactic has its own dedicated page with associated techniques. (Here’s Reconnaissance)
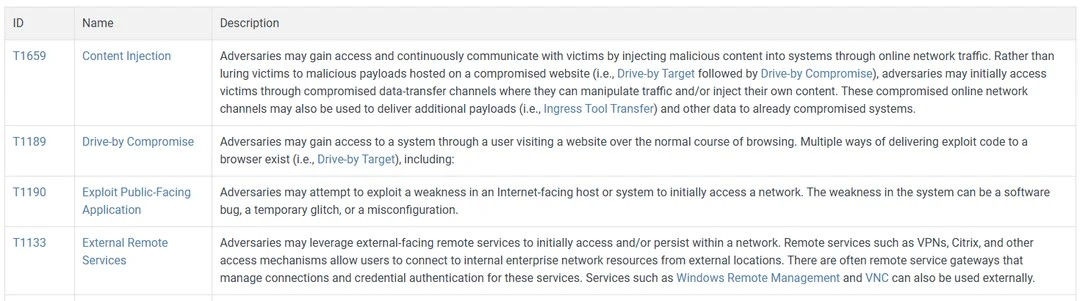
Techniques: This is “how” attackers do what they do. If you are looking into the tactic of initial access, you will find techniques like phishing, supply chain compromise, and ‘external remote services,’ which covers things like VPN and RDP exploits. You can see the techniques associated with initial access here.
Every technique has an ID, which are like the tactic assignment IDs. The external remote services technique is assigned ID T1133. This is a Technique (T) and was the 1133rd technique added to the ATT&CK system.
Procedures: These are specific real-world examples of how different threat groups execute the ATT&CK techniques. If you follow the link to T1133 (external remote services), you’ll find the procedures page for this technique. Here you’ll find lists of attack campaigns, threat groups and malicious software, and how these were used in real attacks. You’ll also find detection and mitigation information.
Why should you care?
Standards and frameworks can help you understand your cybersecurity position. They’re very important when it comes to building a comprehensive strategy and identifying security gaps. They answer questions about what to do and when to do it. MITRE ATT&CK is another tool for you to use in building your security. It gives you detailed information on how threat actors operate. It’s a deep dive into their behavior.
This information can help you research anomalous behavior and see if there are any links to a known threat group or campaign. It can be used to fine-tune your detection rules or test defenses against the TTPs associated with reconnaissance or initial access.
To sum up, think of NIST CSF and CIS standards as what good security looks like. Think of TTPs and ATT&CK as how bad actors actually operate. You need both lenses to build resilient, adaptive defenses in today’s threat landscape.
More:
Note: This article originally appears in the Barracuda Reddit community.

The Ransomware Insights Report 2025
Key findings about the experience and impact of ransomware on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

Managed Vulnerability Security: Faster remediation, fewer risks, easier compliance
See how easy it can be to find the vulnerabilities cybercriminals want to exploit