The new NIST LEV metric: What you need to know
Rising vulnerability reports and an increasing backlog of critical vulnerabilities and exposures (CVE) conspire to put companies at risk. The new NIST Likely Exploited Vulnerabilities (LEV) metric can help. Here's how.
The state of CVE cybersecurity
NIST's CVE program tracks both historic and emerging vulnerabilities to help businesses reduce their cybersecurity risk. According to a recent NIST update, however, the agency is falling behind in processing and classifying new CVEs. In part, this backlog stems from increased reporting volumes. In 2024, CVE submissions rose 32%, and NIST says that "the rate of submissions will continue to increase in 2025."
Manual processes paired with a shortage of skilled professionals also impact the backlog. While NIST plans to increase efficiency by reviewing internal processes and automating tasks where possible, the CVE backlog will likely get worse before it gets better.
This creates a challenge for businesses that rely on CVE data to help inform cybersecurity practices. With cybercriminals constantly exploring new ways to exploit commonly used systems, delays in reporting and analysis create a security gap. Applications and APIs that companies trust may pose undetected risks, giving attackers more time to act without security intervention.
Close but not quite: KEV and EPSS
With CVE reports falling behind, other programs such as the Known Exploited Vulnerabilities (KEV) catalog and the Exploit Prediction Scoring System (EPSS) offer ways to reduce risk.
Understanding KEV
The KEV list is maintained by CISA. It contains more than 1,300 vulnerabilities that have been exploited in the wild. As a result, it's a commonly used source of security information because it helps teams better understand where risk is coming from and how they can effectively respond. Given the sheer number of listed vulnerabilities, however, defending against the entire catalog isn't possible. Instead, teams need to determine which vulnerabilities pose the most risk and take targeted action to prevent compromise.
Exploring EPSS
EPSS was developed in 2018 by security professionals in the Forum of Incident Response and Security Teams (FIRST). This scoring system considers multiple factors including the presence of publicly available exploits, the complexity of exploit processes, the popularity of vulnerable code, and any real-world data gathered from sources such as intrusion detection systems (IDS) or honeypots.
Using this data, EPSS predicts the likelihood that a vulnerability will be exploited over a set timeframe, which is typically 30 days. In addition, the model suggests when risk is highest and lowest over this 30-day period. The most recent version of EPSS was released in March 2025.
Both programs help reduce the risk of compromise, but they also come with caveats. While KEV flags approximately 1,300 vulnerabilities, these security concerns don't carry equal risk. As noted by a recent Security Week piece, analysis of 25 KEV bugs that impact cloud-native applications found that 10 were either technically unexploitable or required extremely specific conditions to execute. As a result, they do not represent immediate or actionable threats. To make the most of KEV data, cybersecurity teams need to consider the context of vulnerabilities — something that takes time and effort away from other security practices.
EPSS, meanwhile, helps companies better understand threat risk by predicting the likelihood of in-the-wild compromise, typically over a 30-day period. The challenge here? Cybersecurity landscapes can change significantly in 30 days, making EPSS useful for longer-term planning but less applicable in day-to-day operations.
How LEV can help level the playing field
LEV offers a new approach to vulnerability management, which focuses on calculating the likelihood that a bug has already been exploited by threat actors, even if this exploitation hasn't been observed.
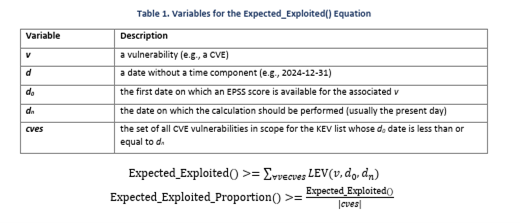
LEV itself is a formula that provides daily updates of:
- The chances that a CVE has already been exploited
- The chances that a CVE will be exploited.
Here's the formula:
With LEV, cybersecurity teams receive data including:
- CVE name, date and description
- Probability of past exploitation
- Maximum EPSS score for selected 30-day windows
- Date of the maximum EPSS score in each of those windows
- A list of affected software or code described using Common Product Enumeration (CPE)
According to the NIST LEV whitepaper: "These results can be used to measure the expected proportion of CVEs that have been exploited and the comprehensiveness of KEV lists. These results can also augment both KEV-based and EPSS-based vulnerability remediation prioritization."
Conquering compromise: A collaborative effort
LEV is a powerful new tool in NIST's cybersecurity arsenal, but it's not a silver bullet. While more information about the real-world implications of existing CVEs helps reduce compromise risk, LEV is more effective when paired with other assets such as EPSS and KEV, and combined with advanced cybersecurity tools such as multimodal AI threat detection.
Collaborative efforts give companies critical information about what's already happened, what's happening right now and what's likely to happen in the coming days or weeks. The result is a more proactive approach to cybersecurity that helps frustrate attacker efforts and stop compromise before it starts.

The Email Security Breach Report 2025
Key findings about the experience and impact of email security breaches on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

The MSP Customer Insight Report 2025
A global look at what organizations need and want from their cybersecurity managed service providers