Rhysida ransomware: The creepy crawling criminal hiding in the dark
Today, we're looking at Rhysida ransomware, a ransomware-as-a-service (RaaS) operation that employs double extortion to force victims to pay a ransom. Rhysida was first observed in May 2023 but was later found to have been in operation since January of that year.
Rhysida is still active today and has posted 91 victims on its leak website. Activity from this group surged in November 2023 and has reduced since then. The most recent victim is Unimed Vales do Taquari e Rio Pardo (Unimed), who has been given seven days to pay before Rhysida publishes the stolen data.
Who is Rhysida?
The Rhysida operation is clearly driven by financial motives, but there is little else known about this ransomware group. It does not appear to be affiliated with any nation-state or attached to any political ideology. Researchers believe the group is located in Russia or in the Commonwealth of Independent States (CIS), which is a group of nation-states that were formerly part of the Soviet Union. This is based on several observations, such as the primary language of internal communications (Russian) and the presence of Russian words and phrases on the Rhysida leak site. The group targets companies in all countries except those located in Russia and other CIS states. This suggests they are within the reach of Russian or CIS law enforcement.
The group takes its name from the Rhysida genus of centipedes, which analysts have speculated is meant to project an image of stealth and shadows. Some Redditors playfully entertained the idea that the name was an homage to Jack Rhysider, who is the brains and voice behind the excellent Darknet Diaries podcast. I doubt that anyone took that idea seriously, but just in case, here's a screenshot from the Rhysida leak site:
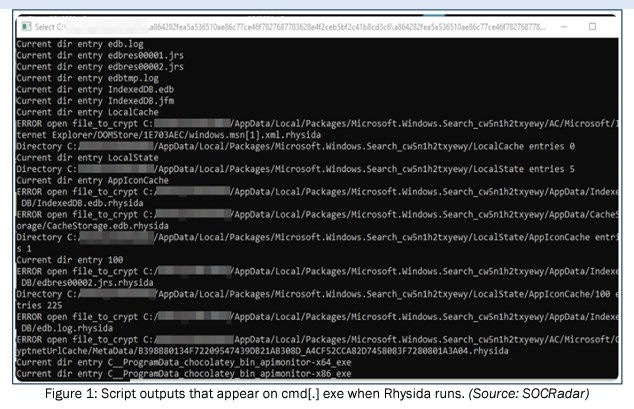
In August 2023, the Health Sector Cybersecurity Coordination Center (HC3), an agency within the U.S. Department of Health and Human Services (HHS) issued a sector alert on Rhysida ransomware and the heightened threat to healthcare and public health organizations. In this report, HC3 stated that Rhysida ransomware appeared to be in the early stages of development, and other analysts noted that 'samples continue to lack commodity features like VSS Removal, multiple persistence mechanisms, process termination or unhooking.' This aligned with other analysts who speculated that Rhysida was 'novice malware' because the attack was visible to the end-user. Here's a screenshot of the attack in action:
Mature attacks are designed to operate in the background and remain hidden from view. Novice malware attacks are less sophisticated and easier to detect and mitigate. Rhysida unfortunately proves itself to be a more advanced threat just a few months after the HC3 alert is published.
How Rhysida works
Rhysida operators use a number of methods to gain access and establish themselves within a system. Here are some of their favorites:
- Spear Phishing with malicious attachments that execute malware or redirect them to a malicious site that facilitates the download of malware.
- Exploiting unpatched vulnerabilities in web servers, email servers, or other network infrastructure.
- Attacking remote desktop protocol (RDP) and virtual private network (VPN) access points. To gain entry through these access points, attackers may use stolen credentials, credential stuffing, vulnerability exploits, or brute-force attacks.
- Hijacking or deploying legitimate administrative tools such as PowerShell, WinSCP, Cobalt Strike, PsExec, and others for initial access and to facilitate lateral movement within the compromised networks.
Depending on who you ask, either phishing or RDP attacks are the primary methods of initial access, but Rhysida is capable of using many different methods.
Once Rhysida is in the system, they will elevate their attack by installing their custom malware and preparing for the encryption event:
- Privilege escalation is attempted to gain higher-level permissions on the network. This gives them many more capabilities, including the ability to dump and capture Windows network credentials.
- Lateral movement is initiated as soon as possible but is usually more effective after privileges have been escalated. At this point, they gather information on the systems and data and spread malware throughout the system to prepare for a widespread attack.
- Data exfiltration is the next step. Rhysida steals data from the system prior to launching the encryption. This allows them to threaten to release the stolen data if the victim refuses to purchase a decryption key.
Now we're at the point of encryption.
- The Rhysida ransomware binary is executed using PsExec, which is a system tool that allows you to run programs on remote systems. This helps them expand the 'blast radius' through the network. The ransomware leaves server and workstation data encrypted and renamed with a .rhysida file extension.
- A ransom note is dropped on the infected systems. The note leaves instructions for payment and states that the 'cybersecurity team Rhysida' is notifying the victim of a detected breach:
The ransom note is a PDF named 'CriticalBreachDetected.pdf.'
From here the extortion proceeds like most other ransomware attacks: victims are told how to pay the ransom and given a timeline before their data is published or sold. The victim's name is published on the Rhysida leak site along with screenshots or select chunks of stolen data. This sets up the full double-extortion play.
Rhysida also tries to maintain its presence in the network to monitor the situation, enforce its demands, and prepare for future attacks.
Rhysida's custom ransomware
One of the interesting things about Rhysida is that although it appeared to be novice malware as late as August 2023, it was described as sophisticated malware as early as October 2023. In February 2024, researchers from Kookmin University and the Korea Internet and Security Agency (KISA) discovered a vulnerability in Rhysida's ransomware source code. These researchers published detailed information on the vulnerability and a proven decryption method.
Security researchers have observed Rhysida's ransomware using a self-deletion mechanism that removes the ransomware binary from the system after encryption. This hides information about the attack and complicates forensic analysis. Rhysida is also compatible with pre-Windows 10 versions of Microsoft Windows. This broadens the potential target base by a few percentage points. A quick guesstimate based on market share and other data says this backward compatibility exposes an additional 63.3 million Windows systems. The real number is hopefully not that high though. Many of those systems are probably isolated or finally being replaced as Windows 10 nears end-of-life. It's still a risk, and if you are running these older end-of-support systems, the backward compatibility of Rhysida is another reason to update.
Notable victims
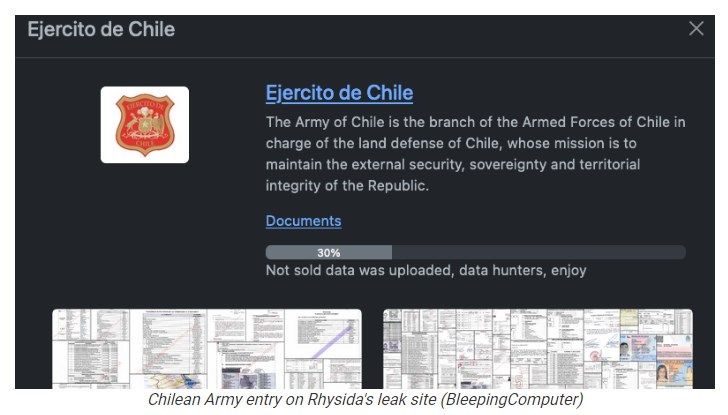
Rhysida attacks companies in all economic sectors. The group captured the attention of the security industry with its successful breach of the Chilean Army, which was discovered by Chilean Army officials over the weekend of May 27, 2024. Rhysida gained access through a phishing attack and ultimately leaked about 30% of the documents it claims to have stolen.
Rhysida has also had several significant healthcare victims, including Unimed (mentioned above), Prospect Medical Holdings and Lurie's Children's Hospital. The Prospect Medical Holdings attack impacted 17 hospitals and 166 clinics across the United States. Rhysida claimed to have exfiltrated 1.3 terabytes of SQL databases and one terabyte of documents. Security Boulevard compiled this sequence of events related to the attack:
- Rhysida ransomware started seeding the attack by spreading infected files via phishing emails and Cobalt Strike.
- August 3, 2023 Prospect employees become aware of the attack, with staff discovering their computers are disabled by ransomware.
- Later that day, Prospect began shutting down systems and network links to contain the incident.
- As a result, all patient records and management must revert to paper, slowing treatment and impeding care.
- Prospect began the arduous process of restoring systems to functionality and re-establishing network connectivity across their organization.
- August 24, 2023, Rhysidia claims credit, advertising their stolen goods on the dark web.
- September 2023, Prospect announces that their “computer systems are now back up and running”
- For the next few months and possibly years, Prospect will be investigating the full scope of the attack and managing HIPAA-related fallout from the incident.
Rhysida successfully attacked the British Library in November 2023, encrypting files and stealing roughly 600GB of data including sensitive personal details of library users and staff. The operational disruptions to the library continued into 2024, and the recovery costs were estimated at $7.5 - 8.7 million. The library decided against paying the ransom, which was less than $1 million at the time.
The British Library has released a detailed incident review here. One of the key takeaways is this paragraph on page 2 of the report:
"Our major software systems cannot be brought back in their pre-attack form, either because they are no longer supported by the vendor or because they will not function on the new secure infrastructure that is currently being rolled out. This includes our main library services platform, which supports services ranging from cataloguing and ingest of non-print legal deposit (NPLD) material to collection access and inter-library loan. Other systems will require modification or migration to more recent software versions before they can be restored in the new infrastructure. Our cloud-based systems, including finance and payroll, have functioned normally throughout the incident."
(emphasis mine)
I point this out because we've discussed the risk of legacy systems and the difficulty of securing them. If you are looking for some justification to help you get a budget to upgrade your systems, this report might be of assistance.
In December 2023, Rhysida struck gold with the successful attack of Insomniac Games, which is a video game developer that was working on the "Marvel's Wolverine" game at the time. The stolen data turned out to be a treasure for the criminals. The data included internal HR documents, employee passport scans, screenshots of Slack conversations, details of upcoming projects, and non-disclosure agreements and other contracts. While hardcore criminals are going for the personal files, your average everyday pirate is there for the games that were leaked as part of the data. There is still an active subreddit dedicated to the sharing of the leaks from "the Great insomniac and PlayStation hack of December 2023."
Rhysida family tree
Rhysida and Vice Society are connected in some way, but opinions differ on their relationship. Most reports have concluded that Rhysida is a rebrand of the former group.
The connection between Vice Society and Rhysida is based on overlapping tactics and their occasional use of each other's ransomware payloads. Rhysida's methods of encryption and the structure of its ransomware notes are also similar, and Rhysida has been observed using the servers and domains that were used by Vice Society.
Vice Society is a double-extortion ransomware actor that emerged in 2021 and quickly became one of the top threats to the education sector, especially public schools. You may recall the name from its massive attack on the Los Angeles Unified School District (LAUSD) in 2022. LAUSD did not pay the ransom, and Vice Society made good on its threats. The attack caused significant disruption and resulted in the leak of thousands of student and employee records. An independent analysis by The 74 revealed that approximately 2,000 student psychological reviews were included in the leak.
Unlike many ransomware groups, Vice Society is a closed group that does not have affiliates and does not operate as a RaaS. It is thought to be a Russian-based organization.
Vice Society activity started to taper off just as Rhysida emerged. For this reason and the others listed above, it is widely accepted that Rhysida's origins are with Vice Society. What is strange about this is that the Rhysida custom malware was considered 'basic' when it first hit the scene. As mentioned in the 'Who is Rhysida' section, the ransomware was thought to be novice malware. That seems unusual for a threat actor with successful attacks on high-profile targets in education, healthcare, and other sectors.
Vice Society also listed San Francisco Bay Area Rapid Transport (BART) on its leak site in January 2023. BART did not pay the ransom, and approximately 120,000 documents were leaked. These files were stolen from the BART Police, and they included some potentially damaging and embarrassing information:
The files include unredacted reports detailing suspected child abuse, including the children’s names and birth dates, and in some cases, the descriptions of the adult and the alleged child abuse incident.
The leak also exposed mental health record forms that the transit police department could use to recommend someone for mental health evaluation, reports linking named suspects to various crimes, BART contractors’ names and driver’s license numbers, and recruitment candidates’ documents.
It seems odd that a group so experienced would evolve into a group using novice malware. But Rhysida did improve their ransomware very quickly, and maybe that was because they picked up a few experienced threat actors from Vice Society.
What's next?
The timelines of Vice Society and Rhysida overlap, just like their tactics. There hasn't been much news about Vice Society since August 2023, when researchers realized the connection between the groups.
The problem with names like Vice Society and Rhysida is that they're just temporary brands for clusters of individual threat actors who can easily move from one to another. The threat clusters behind the brands are always active, even when the brand shuts down or simply fades out.
The best way to defend against ransomware families like Rhysida is to adopt a zero-trust mindset. Assume that everything is an attack and verify everything all the time. The U.S. Cybersecurity and Infrastructure Agency (CISA) recommends companies do the following right away:
- Prioritize remediating known exploited vulnerabilities.
- Enable multifactor authentication (MFA) for all services to the extent possible, particularly for webmail, VPN, and accounts that access critical systems.
- Segment networks to prevent the spread of ransomware.
There is more information in the CISA advisory published here.
Barracuda can help
Only Barracuda provides multi-faceted protection that covers all the major threat vectors, protects your data, and automates incident response. Over 200,000 customers worldwide count on Barracuda to protect their email, networks, applications, and data. Visit our website to explore our comprehensive cybersecurity platform.

The Email Security Breach Report 2025
Key findings about the experience and impact of email security breaches on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

The MSP Customer Insight Report 2025
A global look at what organizations need and want from their cybersecurity managed service providers