
API discovery is key to securing your applications
API Trends
The application programming interface (API) has been picking up pace in the past few years which is becoming visible in the overall API traffic received by application servers. Based on the 2023 State of API report by Postman, 121 million collections have been created for the API ecosystem, and there were 1.29 billion new GET requests in the 12 months leading up to May 2023. As the world is moving towards API-first development, it is also starting to realize many new challenges to secure web servers to provide apt security for APIs.
API Security Challenges
During application development, programmers add/update/delete APIs very regularly. Due to this, administrators find it very difficult to maintain appropriate security rules to match those evolving API sets. The majority of APIs are created for private and partner integration purposes, where security is not a development priority. This further increases the risk of API security taking a backseat.
Another notable fact is that 97% of the application owners are aware of the need for improvements in API security but are not able to achieve that due to a lack of visibility in API endpoints and structures.
We tried to summarize major issues faced by web application owners in deploying and securing their APIs.
- Unprecedented rise in API traffic
- Based on the 2023 State of the API Report, the total number of requests created is increasing drastically as can be seen from the chart below:
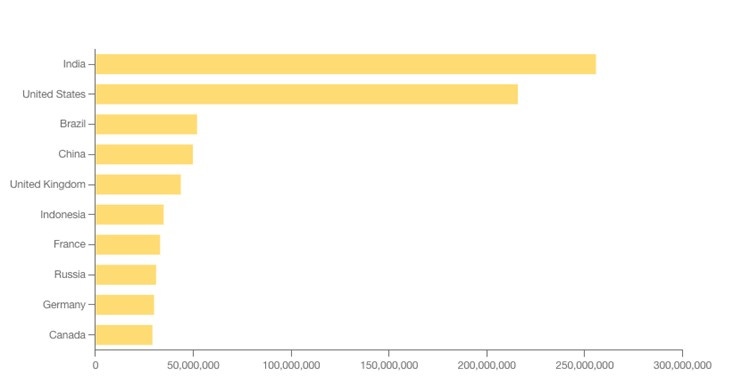
- Lack of awareness and documentation of public and private API endpoints.
- As companies are moving towards API-first development, new API endpoints keep getting created, and the old ones become obsolete without much knowledge to the administrator. With little or no information about those, administrators find it difficult to configure/reconfigure web servers for best security practices leaving many security gaps in the system.
- Use of internal APIs
- Barracuda research has revealed that more than 25% of APIs are designed to be internal only APIs. These internal APIs are often developed with significantly less focus on security. In many cases, APIs are considered “hidden” (by the development teams) behind the web applications, and application owners are not aware when these internal APIs are exposed to the outside world. This results in big security holes and a growing attack surface – particularly if the applications are accessible through the internet or do not have access controls to prevent lateral movement by a threat actor.
- Identifying Shadow or Zombie APIs
- There are several APIs that are created in the system for testing purposes and unknowingly left behind without any security in place. Following traffic trails to such APIs becomes almost impossible due to limited traffic arriving at those testing APIs. Furthermore, it is very common for application developers and administrators to miss out on minor changes leading to security rules not being up to date always. Barracuda research has found that close to 37% admitted lacking an understanding of API standards. If attackers can identify these endpoints, as they did with Optus, they can then exploit the API; they can cause serious damage to the application server and cause a breach of user data.
- Identifying all available API endpoints and structures
- Without live traffic analysis, it is very easy to miss API endpoints exposed by the server as well as the structure of individual parameters expected by the API. Without complete knowledge of these, we can never be confident about the security needs of each endpoint and parameter, which eventually leads to insufficient security configuration.
- Most attacked APIs / Parameters
- There are some APIs, such as login APIs, that are attacked more than others. Similarly, username/password fields are typically more prone to ingestion attacks than other parameters. But without exact information about all the fields, number of queries, value formats, etc., it becomes a big challenge for administrators to deploy APIs in a safe manner against possible exploits.
The threats posed by the upsurge in APIs are increasing the workload for IT teams. Alongside this growth in APIs, companies are facing increasingly sophisticated cyberattacks across other threat vectors, and a shortage in the cybersecurity workforce. This makes it difficult and expensive for companies to fully staff internal IT teams and keep the company fully secured.
Barracuda WAF API discovery
Barracuda’s Machine Learning-powered API Discovery analyses all traffic arriving at your application, filters the API traffic, and uses this information to identify API traffic endpoints. Once these endpoints are identified, it then learns the structure of the keys/values expected by each API. At this point, Barracuda Application Protection will auto-configure security settings to ensure your APIs are protected against the latest threats originating in the market. API owners and administrators can then preview and fine-tune these configurations as desired.
Barracuda Application Protection further leverages machine learning (ML) to continuously learn and secure your application environment. The Auto Configuration Engine is a Barracuda Active Threat Intelligence service that reviews all your application traffic from connected units and provides application-specific configuration recommendations. This helps you close Web Application and API-related security gaps while reducing the IT overhead assigned to application protection.
You can find more information about Barracuda Application Protection on our website. You can also get a free 30-day trial to test the solution in your own environment.

The Managed XDR Global Threat Report
Key findings about the tactics attackers use to target organizations and the security weak spots they try to exploit
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

The Email Security Breach Report 2025
Key findings about the experience and impact of email security breaches on organizations worldwide

