
Active ransomware attack uses impersonation and embedded advanced threats
In the last 24 hours, the Barracuda advanced security team has observed about 20 million attempts at a ransomware attack through an email attachment "Payment_201708-6165.7z." Here is a screenshot of the email with the addresses redacted:
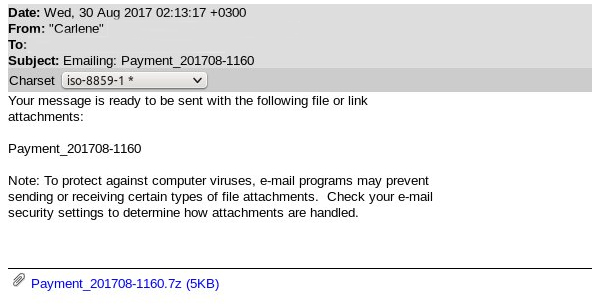
This attachment is a JavaScript file in a 7zip archive that the Barracuda ATP Dynamic Analysis Layer identifies as a "file-encryption/ransomware" type virus.
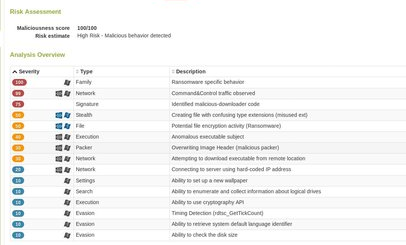
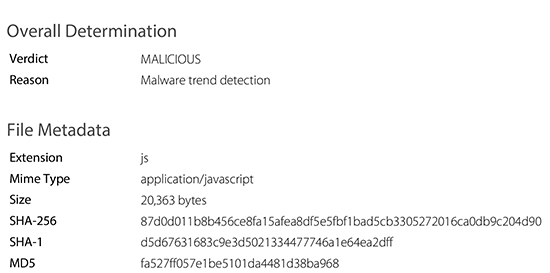
Delivery: The attachment arrives in the inbox. It's best to stop this attack before it arrives at your network, which is possible with an email security service such as Barracuda Essentials for Email Security and Advanced Threat Detection.
Infection: As you can see by the spoofed source address, this attack relies on impersonation to gain the trust of the recipient. If the impersonation is successful, the recipient is likely to open the Payment file attachment. At this point, the embedded threat may be executed, which will begin the process of encryption.
Ransom: Once the ransomware attack reaches a pre-determined threshold, it will present a document that demands a payment for the decryption file. At this point, the victim might pay the ransom, recover from backup, or search for a decryption key online from a resource like NoMoreRansom. We advise against making payment to ransomware criminals because this doesn't guarantee the decryption of your files and it encourages them to target you again in the future.
Barracuda Advanced Threat Protection stops this attack prior to the delivery phase. Customers with Barracuda Essentials for Email Security and Barracuda Essentials for Office 365 are fully protected against this attack.
For more information on Barracuda Advanced Threat Protection, visit the corporate website here.
 Eugene is the Lead Platform Architect working on deep-learning technology for Barracuda, and leader of the Barracuda Content Intelligence Team. Connect with him on LinkedIn here.
Eugene is the Lead Platform Architect working on deep-learning technology for Barracuda, and leader of the Barracuda Content Intelligence Team. Connect with him on LinkedIn here.

The Ransomware Insights Report 2025
Key findings about the experience and impact of ransomware on organizations worldwide
Subscribe to the Barracuda Blog.
Sign up to receive threat spotlights, industry commentary, and more.

Managed Vulnerability Security: Faster remediation, fewer risks, easier compliance
See how easy it can be to find the vulnerabilities cybercriminals want to exploit




